A Comprehensive Guide to Phishing: Types of Phishing, Prevention, and Response Tips
Hey there cybersecurity pros,
Phishing – it’s the oldest trick in the book yet remains one of the most persistent cybersecurity threats today. Did you know that there are many types of phishing attacks, from spear phishing to whaling, and each requires a unique approach to prevention? Despite our best efforts, those dastardly phishers continue finding new ways to bait unsuspecting victims and evade even advanced detection systems.
To effectively prevent phishing attacks, it’s essential to understand how to prevent phishing in the first place. One crucial step is to avoid clicking on suspicious links, also known as phishing links, which can download malware or steal sensitive information. But what if you accidentally open a phishing email? Don’t panic! Knowing what to do if you open a phishing email can make all the difference in minimizing the damage.
But we’re not going down without a fight! In this comprehensive guide, we’ll break down everything there is to know about phishing so you can shore up those defenses and finally gain the upper hand against would-be attackers. You’ll learn how can you stop phishing emails from reaching your inbox in the first place, and what measures to take to prevent phishing attacks from succeeding.
Understanding Phishing: The OG Cyber Attack
Let’s start from square one – what exactly is phishing? Phishing is one of the most common types of phishing attacks, where attackers send fraudulent communications that appear to come from a trustworthy source. The goal is to trick recipients into handing over sensitive information or installing malware. This is where knowing how to prevent phishing attacks can save you from a lot of trouble.
The most common phishing technique is via email, where the attacker spoofs the “From” address so the message seems to originate from a legitimate organization. They’ll use urgent language and lead recipients to a fake website that mimics a real one, often including a phishing link that can compromise your security. Once on the site, users are prompted to enter account credentials or personal data that the hackers can then steal.
But what to do if you open a phishing email? Stay calm and don’t panic. Don’t enter any sensitive information, and don’t click on any suspicious links. Instead, report the email to the relevant authorities and change your passwords immediately.
Other popular phishing mediums include:
- Spear phishing – Highly targeted phishing attacks against specific individuals in an organization. The message content is customized with familiar names/logos and inside information to make it more convincing.
- Whaling – Spear phishing directed at senior executives like CEOs and CFOs. The big kahunas are high-value targets.
- Vishing – Phishing over the phone. Attackers call up impersonating banks/technical support and get users to hand over sensitive info. No Nigerian prince inheritance scams here!
- Smishing – Phishing via SMS text. A link in a text leads to a dodgy website asking for logins or bank details. Short, sweet, and to the point!
- Clone phishing – The attacker spoofs an existing email thread by replying to all and including a malicious link/attachment. Instills false confidence if it’s a conversation the victim recognizes.
So, how can you stop phishing emails from landing in your inbox in the first place? Be cautious with emails that ask for personal information, be wary of generic greetings, and never click on suspicious links. By being proactive and knowing how to prevent phishing, you can avoid falling prey to these types of phishing attacks.
As you can see, phishing is constantly evolving and limited only by the attacker’s imagination. But at its core, it preys on human nature – our tendency to trust and our desire to avoid negative consequences like account suspension. This leads perfectly into how to spot those sneaky phishing attempts…
Identifying Phishing Attempts: Types of Phishing and How to Prevent Phishing Attacks
The first line of defense against phishing is vigilance – being able to quickly recognize an attack before you become compromised. Here are the telltale signs of a phishing email or message, and understanding what a phishing link is can help you prevent phishing attacks:
Sense of urgency – Subject lines will say “Urgent notice!” or “Your account will be suspended”. Time pressure is applied to get users to act impulsively. This tactic is commonly used in phishing attacks, making it essential to know how to prevent phishing.
Unknown sender – Check that the sender email aligns with the company/org being spoofed. Attacker emails often have slight misspellings. This is a common trait of phishing emails, and being cautious of unknown senders can help you stop phishing emails.
Generic greetings – Impersonal greetings like “Dear user” instead of your name. Indicates mass targeting, which is a characteristic of phishing emails.
Spelling/grammar errors – Sloppy errors show a lack of effort to mimic legitimate comms. Phishing emails often contain errors, making it crucial to be vigilant.
Veiled threats – Language threatening account closure or legal action if you don’t respond. Fearmongering at its finest! Phishing attacks often use threats to create a sense of urgency.
ODD embedded links – Don’t just glance at text links! Hover over to preview the actual URL for anything suspicious. Knowing how to prevent phishing attacks can help you avoid falling prey to these tactics.
And if you want visual examples, here are two phishing emails:
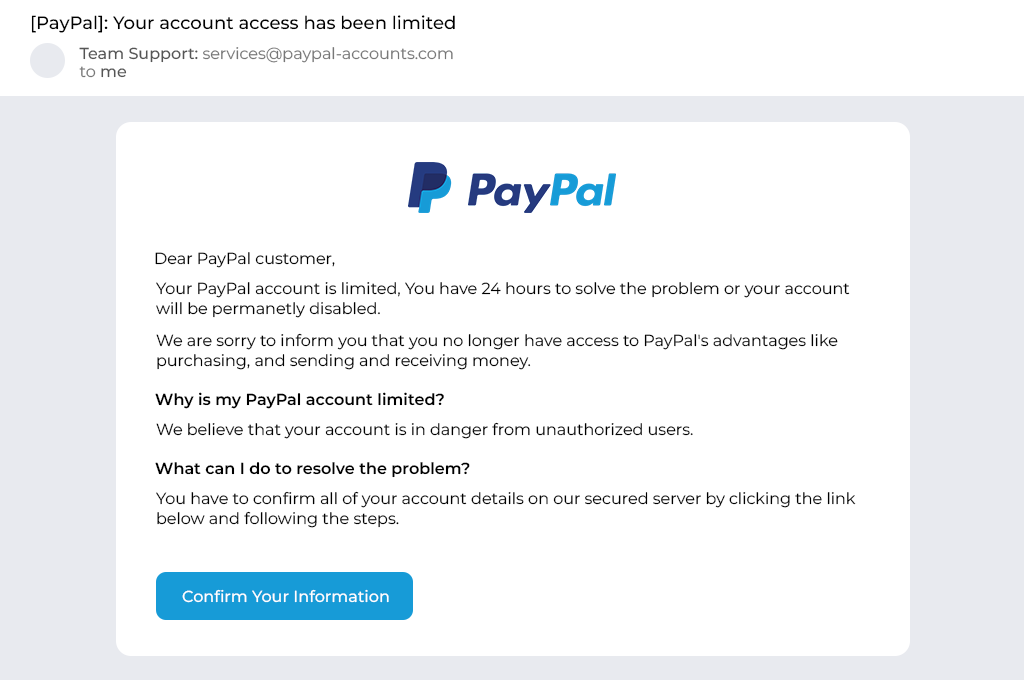
This email looks legit at first glance with PayPal colors/logos. But the sender is a free webmail account, not PayPal. A dead giveaway of an amateur attempt!
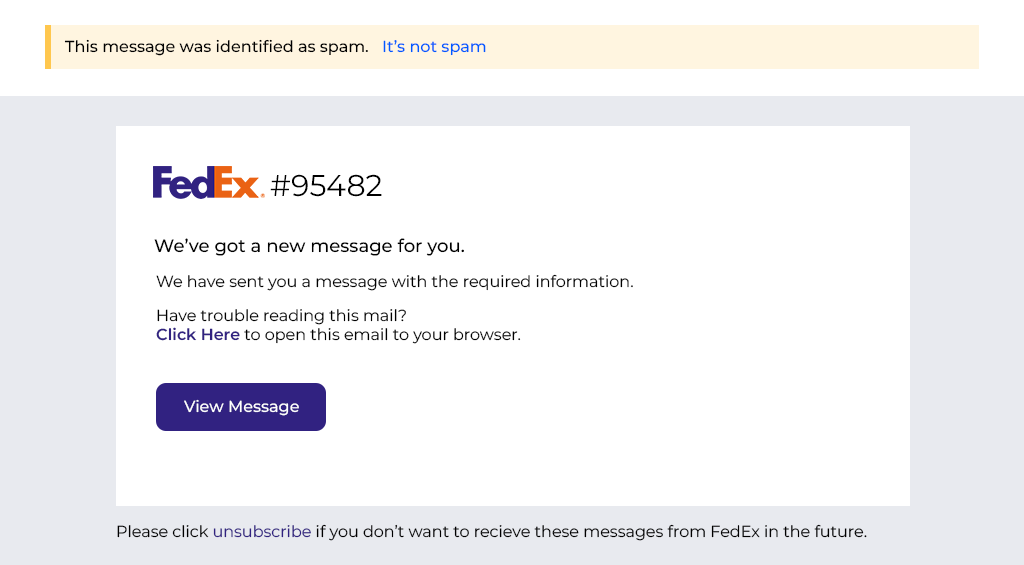
This is a more sophisticated phishing email that mimics package tracking notifications from FedEx. But again, hovering over the tracking link reveals a sketchy URL unrelated to FedEx. Nice try, scammer!
When evaluating links themselves, look for:
- Mismatched URL – The link text says one thing, but leads somewhere completely different
- Weird subdomains – Beware links with extra subdomains inserted like “billing-update.paypal.secure.com“
- Deceptive URLs – The attacker uses URL shortening services to hide the true landing site
So in summary, let your skeptical spidey senses tingle with anything urgent, unusual, or just off. If your gut says it’s weird, it just might be phishing.
Preventing Phishing Attacks
Now that you know what to look for, let’s talk about proactive measures for avoiding types of phishing attacks in the first place. How to prevent phishing requires a combination of technological safeguards and human vigilance.
On an individual level, you can:
- Never click links or attachments from unknown/untrusted sources, which can lead to what is a phishing link that can compromise your device
- Verify the legitimacy of websites before entering any information to avoid falling prey to phishing scams
- Use a password manager to avoid reusing credentials on random sites, making it harder for phishers to gain access
- Backup data regularly in case malware makes it onto your device, which can happen if you don’t know how to prevent phishing attacks
For organizations, best practices include:
- Security awareness training to educate employees on phishing red flags and types of phishing tactics
- Simulated phishing tests to gauge staff readiness to report real attacks and improve their understanding of how to prevent phishing
- Web filtering that blocks access to known phishing sites and IP addresses, reducing the risk of what is phishing link infections
- Email authentication protocols like SPF, DKIM, and DMARC to catch spoofing and prevent how can you stop phishing emails from reaching your inbox
- Endpoint detection that identifies malware and anomalous activity from phishing links, helping you to prevent phishing attacks
Multi-factor authentication (MFA) also adds a critical layer of protection should phishers compromise a password through social engineering. By requiring an additional step to log in from a new device, MFA blocks attackers out of accounts even with stolen credentials in hand.
The bottom line, a combination of technological safeguards and human vigilance gives you the best armor against phishing.
A Side, But Super Important Tip for Readers
Phishing is a big problem these days. Scammers are getting better at tricking people to click on bad links or hand over private information. Their phishing scams are getting harder to spot. But AI technology could help stop these phishing attacks.
As the “AI Security” blog post talks about, AI can look through way more data than a person can. It can notice suspicious patterns that humans might miss. So, AI can catch tricky phishing emails before you even see them in your inbox.
So, if you worry about getting scammed by phishing lies and your money or info getting stolen? You should think about getting AI to protect you. I believe AI can smash those phishing crooks! Don’t just take my word for it — check out that blog post to learn more about how AI beats phishers at their own game.
Responding to Successful Phishing
But what happens if a phishing attempt succeeds and a staff member is compromised?
Firstly, immediately report the incident to your IT/security team. Provide any details you have like sender address, subject line, time received, etc. to aid in identifying other victims. If you’re wondering how to prevent phishing attacks, this is the first step.
If you click a link or download an attachment, isolate the affected device and stop using it for any sensitive transactions. Run a full antivirus scan to uncover any potential malware installed. In dire cases, the machine may need to be wiped and reset completely to factory settings.
Reset all account passwords accessed from that device if malware could have captured your credentials. If banks or financial accounts were involved, proactively contact them regarding fraudulent activity.
Monitor your credit and existing accounts closely in the following weeks for signs of misuse. And don’t beat yourself up – anyone can slip up when faced with a convincingly crafted phishing attempt.
For email in particular, phishing prevention doesn’t end when a malicious message slips into your inbox. Here are steps to contain the damage:
- Set up email filtering rules to auto-delete messages from the phisher’s address
- Block the sender at your email server level if possible
- Use the “Block Sender” option in your email client to prevent future mail from the attacker
- Report the phishing email to your email provider and cybercrime authorities
- Implement DMARC, DKIM, and SPF to authenticate future emails and reject spoofing
- The nuclear option is to completely block communication from the impersonated domain. But use caution as this could have unintended business consequences.
By following these steps, you can reduce the risk of how can you stop phishing emails and protect your organization from phishing attacks.
Why AI is Critical for Robust Anti-Phishing
As phishing tactics get more advanced, so must our defenses. This is where artificial intelligence and machine learning come into play big time. There are several types of phishing attacks that can be devastating, but with AI-powered cybersecurity, we can stay ahead of the game.
Legacy rules-based security tools are ineffective at spotting novel threats, such as phishing links that redirect users to malicious sites. They rely on matching known malicious patterns – looking for that Nigerian prince we all know and love! But with the rise of sophisticated phishing attacks, it’s essential to know how to prevent phishing by using intelligent and adaptable security tools.
AI-powered cybersecurity is intelligent and adaptable. It uses deep learning algorithms that continuously analyze new threat data and update detection models autonomously. This enables organizations to prevent phishing attacks by detecting phishing emails with new spoofed brands, fresh redirected URLs, and sneaky new malware. Human analysts just can’t keep up with assessing exponentially growing attacks at a machine scale. However, AI security works 24/7 to detect phishing emails and prevent them from causing harm.
Now some may fret about possible ai security risks and machines going rogue! However ethical AI development with human oversight at Beyond Key ensures responsible innovation that enhances phishing protection. With AI, we can finally counter rapidly adapting threats like phishing.
Phishing Attacks: A Growing Concern for Businesses
According to Microsoft, 74% of businesses powered by Microsoft faced a breach last year, resulting in financial losses and reputational damage. At Beyond Key, we understand the importance of protecting your business from these attacks.
Our Cybersecurity Services: Your Shield Against Phishing
Our comprehensive cybersecurity services are designed to safeguard your business from phishing attacks. Our experts will:
- Conduct risk-based benchmarking and gap analysis to identify vulnerabilities
- Develop a remediation plan to mitigate threats
- Implement information security roadmaps to enhance long-term security posture
Don’t Let Phishing Attacks Compromise Your Business
Contact us today to learn more about our cybersecurity services and protect your business from phishing attacks.
The Ongoing Battle Against Phishing
Phishing is one of those persistent problems in cybersecurity that will likely never disappear completely. As long as hackers can profit from social engineering, they’ll keep dreaming up new types of phishing tactics to trip up users and bypass security tools. But savvy cyber pros can gain the upper hand on phishers by deploying a layered defense of awareness training, technological safeguards, and AI-augmented threat detection. With vigilance and the right precautions, organizations can dramatically reduce their risk of phishing compromises.
If you do happen to open a phishing email, don’t panic! Knowing what to do if you open a phishing email is crucial to minimizing the impact. And to prevent phishing emails from reaching your inbox in the first place, it’s essential to know how can you stop phishing emails. By following best practices and using AI-powered security tools, you can significantly reduce the risk of phishing attacks.
And remember, it’s not a matter of if you’ll get phished, but when. Maintaining constant readiness to identify and respond to attacks is key to minimizing impact. Share this guide with your team to ensure everyone has the know-how to help your organization stay resilient.
Let’s keep outsmarting those phishers together! Over and out.